iiNet phishing scam
September 2019
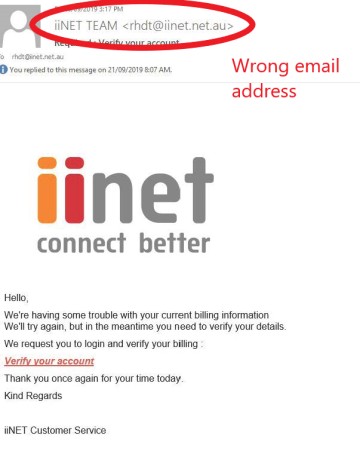
iiNet customers are the target of an email phishing scam.
The email address is spoofed and the address it comes from ends in the exact same way as a true iiNet email address would: @iinet.net.au
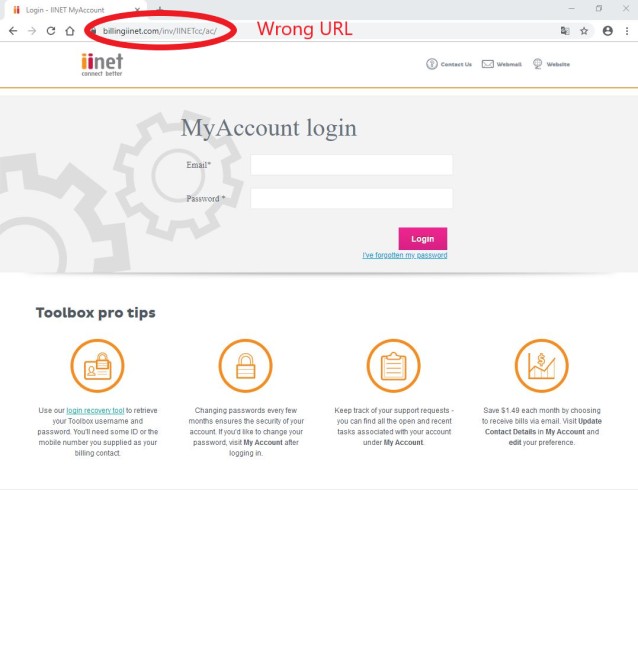
It has a link that takes you to a fake version of the iiNet login – on the screen the url ends in .com.au instead of .net.au
It’s phishing for your account login details and credit card number.
Do NOT click the link. More sure any bills you receive from iiNet come from billing@iinet.net.au – if in doubt contact iiNet to check if a bill is the real deal. Call iiNet Billing support on 13 22 58.
If you’ve clicked a dodgy link in a fake iiNet bill you should:
- run anti-virus software on your device
- report the scam to iiNet
- tell your bank if you’ve allowed scammers access to your credit card details
WA ScamNet has reported this scam to iiNet.
We’re alerting Western Australians because the spoofing of the email address makes this look authentic.
iiNet alert over security breach
Perth internet provider iiNet is investigating a possible security breach after details were posted on social media about the sale of a database allegedly containing information of over 30,000 Westnet client accounts. Westnet was aquired by iiNet in 2008.
A Twitter user named 'CyberWar_News' posted a screenshot showing an anonymous user on an online forum saying:
"There is a shitton [sic] of data inside the database to where I haven't even bothered to dump the whole thing but there is a lot of valuable data inside like cleartext passwords etc. For those who are interested can contact me via jabber below."

iiNet Chief Information Officer Matthew Toohey has stated that they believe the incident may be the result of unauthorised access to legacy Westnet systems.
"The incident has been reported to relevant law-enforcement agencies and is currently under investigation," he said. "Customer username, address, telephone and, in some cases, password information may have been accessed, however, no payment details were stored on the server."
"The system is now offline and at no further risk."
The 30,827 impacted customers had been contacted and told to change their passwords, and additional steps have been taken to monitor impacted accounts.